Measuring Success in Cyber Incident Response: Key Metrics and Strategies
Peter Ferdinand Drucker, an Austrian American management consultant had said,
“What gets measured, gets managed.”
This stands true for your organisation as well. While devising an efficient strategy to combat and prepare for cyber threats is imperative, it is only half the battle won. The other half lies in measuring its success. This is where the role of cyber incident response metrics comes into play – in quantifying the effectiveness of your organisation’s incident response efforts.
These metrics help to identify areas for improvement, justify resource allocation, and highlight the value of your cybersecurity program to stakeholders.
In this blog post, we will talk about cyber incident response metrics, exploring what they are, why they matter, and how to measure success effectively.
What Are Cyber Incident Response Metrics?
Cyber incident response metrics are quantitative measures used to assess the performance and effectiveness of your organisation’s response to cybersecurity incidents. These metrics provide insights into various aspects of the incident response process, such as detection, containment, eradication, and recovery. By tracking these metrics over time, you can evaluate the efficiency of your organisation’s incident response efforts and make informed decisions to enhance its cybersecurity posture.
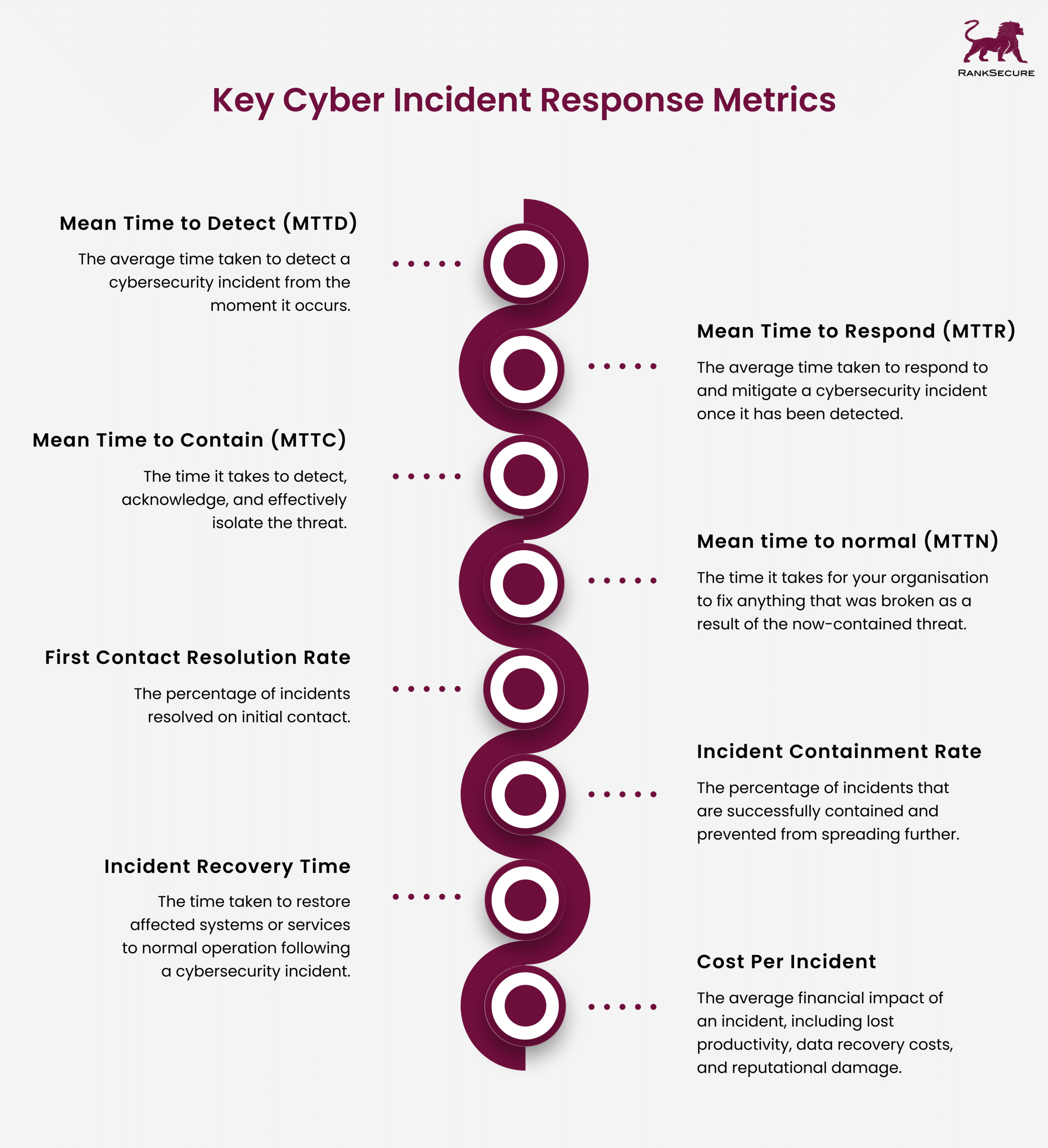
There are various metrics that your organisation can use to measure the success of its cyber incident response efforts. Some of the key metrics include:
Mean Time to Detect (MTTD)
This metric measures the average time taken to detect a cybersecurity incident from the moment it occurs. A lower MTTD indicates a more efficient detection process.
Mean Time to Respond (MTTR)
MTTR measures the average time taken to respond to and mitigate a cybersecurity incident once it has been detected. A lower MTTR suggests a faster and more effective response.
Mean Time to Contain (MTTC)
MTTC takes a more holistic view, including the time it takes to detect, acknowledge, and effectively isolate the threat. A lower MTTC signifies a more efficient response, reducing downtime and business disruption.
Mean time to normal (MTTN)
It defines the time it takes for your organisation to fix anything that was broken as a result of the now-contained threat. A lower MTTN is better, signifying your organisation’s ability to resolve disruptions and get back to business as usual in its service of end users.
First Contact Resolution Rate
This metric tracks the percentage of incidents resolved on initial contact. A high rate indicates a well-trained team with efficient troubleshooting protocols.
Incident Containment Rate
This metric measures the percentage of incidents that are successfully contained and prevented from spreading further within your organisation’s network or systems.
Incident Recovery Time
This metric quantifies the time taken to restore affected systems or services to normal operation following a cybersecurity incident. A shorter recovery time indicates a more resilient and agile response.
Cost Per Incident
This metric calculates the average financial impact of an incident, including lost productivity, data recovery costs, and reputational damage.
Why Do Cyber Incident Response Metrics Matter?
Measuring the success of your organisation’s cyber incident response efforts is essential for several reasons:
Evaluation Of Effectiveness
Metrics help assess the effectiveness of your organisation’s cyber incident response plans and procedures. For example, a lower MTTR signifies a faster recovery, minimising business disruption, and downtime. You can also use other metrics to gauge how well your teams are performing in mitigating cyber threats.
Improvement Of Performance
Metrics provide insights into areas that need improvement. By analysing metrics regularly, your organisation can identify bottlenecks, inefficiencies, and weaknesses in its incident response processes. This information can then be used to refine procedures and enhance overall response capabilities. The incident containment rate, for example, should increase with time, implying that your organisation is employing the necessary steps to respond effectively to cyber incidents.
Allocation Of Resources
Metrics aid in resource allocation by providing data-driven insights into where resources should be invested to improve incident response capabilities. For example, if the mean time to detect a security incident is excessively high, it may indicate a need for better detection tools or additional training for the security team.
Management Of Risks
Understanding cyber incident response metrics helps in risk management by enabling your organisation to quantify the impact of security incidents. Metrics such as the number of incidents, severity levels, and financial losses can help you prioritise your organisation’s response efforts and allocate resources based on the level of risk posed by different types of incidents.
Compliance And Reporting
Many regulatory requirements and industry standards mandate the measurement and reporting of cyber incident response metrics. By tracking and reporting relevant metrics, your organisation can demonstrate compliance with regulations and standards, which is essential for maintaining trust with customers, partners, and regulatory bodies. For example, standards like NIST CSF (National Institute of Standards and Technology Cybersecurity Framework) or ISO 27001 (Information Security Management) provide best practices for cyber incident response and emphasise the importance of measuring and analysing response activities.
How To Measure Success Effectively?
To measure the success of your organisation’s cyber incident response efforts effectively, you should follow these best practices:
Define Objectives And Select Appropriate Metrics
Begin by clearly defining the goals and objectives of your incident response program. Is it minimising downtime, reducing financial impact, or achieving faster incident resolution? Align your metrics with these objectives to ensure relevance and accuracy. You should focus on metrics that provide actionable insights and drive improvement.
Consider these questions:
What kind of attacks is your organisation susceptible to?
What are the specific measures you need to put in place to mitigate them?
Is your team equipped to handle/install relevant measures? If not, do you need to hire an external team to take care of your incident response program?
How much time/resources are you prepared to allocate to this activity?
Collect Quality Data
Ensure that you have reliable data sources in place to collect the necessary information for calculating your chosen metrics, including security logs, incident response tools, and team reports. This data should then be analysed to extract necessary inferences. For instance, the login and log-out activities on your employees’ systems can help determine patterns and possibly identify malicious breach attempts.
Regular Monitoring and Analysis
Monitor your chosen metrics regularly and schedule regular reporting cycles (e.g., weekly, monthly) to track trends and identify areas for improvement. Share your incident response metrics and performance insights with key stakeholders, including senior management, IT teams, and board members. Utilise charts and graphs to present complex data in an easily understandable format for stakeholders.
Benchmark Against Industry Standards
Compare your organisation’s incident response metrics against industry benchmarks and best practices to gauge your performance relative to peers. Identify areas where you fall short and strive to close the gap.
Iterate and Improve
Continuously review and refine your incident response metrics based on feedback and evolving threats. Adapt your measurement approach to reflect changes in your organisation’s cybersecurity landscape and strategic priorities.
An effective incident response goes beyond merely resolving the current issues – it is about leveraging every encounter to strengthen your defences and emerge more resilient than ever.
Tracking your organisation’s cyber incident response metrics is not just important for evaluating its success, but also for gathering valuable intelligence. This intelligence is the key to predicting attacker behaviour, adapting your defences, and maintaining an edge in the relentless race of cybersecurity.
While your organisation can execute response plans and measure their effectiveness in-house, you can also choose to leverage external expertise and resources. By partnering with vendors who provide such services, you can augment your organisation’s internal capabilities to effectively detect, respond to, and recover from cyber threats and security incidents.




