How To Choose A Third-Party Cyber Risk Management Provider
Organisations today rely heavily on third-party vendors for various services and solutions. While outsourcing provides your organisation with flexibility and efficiency, it comes at a cost – cyber risks that can compromise sensitive data and disrupt operations.
A data breach or security incident involving a vendor or third party can have severe repercussions on your organisation, including financial losses, damage to reputation, and regulatory penalties.
💡 Did you know that during 2018-22, Indian private banks reported 205 data breaches while state-owned ones reported 41 breaches? The breaches have caused the banks to incur a loss of ₹1,435 Cr between April 2020 and March 2022.
Moreover, 48% of organisations consider the complexities related to third-party relationships as their primary problem.
This increasing frequency and sophistication of cyber threats has made it crucial for organisations to implement third-party cyber risk management in their processes. However, mitigating these risks is not easy, therefore, most organisations are now turning to vendors who offer risk management services and facilitate ease into the process.
Let us see how hiring vendors to manage your organisation’s third-party cyber risks can benefit your organisation.
The Critical Role of Third-Party Cyber Risk Management Vendors
Ensuring robust third-party cyber risk management practices in your organisation is essential and hiring vendors who offer such services can simplify the process.
Third-party cyber risk management vendors significantly enhance the overall cybersecurity resilience of your organisation and help to effectively manage the risks associated with your external business partners. They protect sensitive data and assets by offering specialised tools, expertise, and services tailored to assess and manage security risks. The range of services they offer includes:
Vendor risk assessment
These vendors conduct thorough assessments of third-party vendors to evaluate their cybersecurity posture, compliance with industry standards and regulations, and overall risk level.
Risk monitoring
They continuously monitor third-party vendors for any changes or developments that may impact their cybersecurity risk profile, such as security breaches, regulatory violations, or changes in business operations.
Due diligence
They perform due diligence on potential third-party vendors before entering into business relationships to ensure they meet your organisation’s cybersecurity and compliance requirements.
Vendor performance management
They track and evaluate the cybersecurity performance of third-party vendors over time to ensure ongoing compliance and adherence to security best practices.
Incident Response and Remediation
They assist your organisation in responding to cybersecurity incidents involving third-party vendors, including incident investigation, containment, and remediation efforts.
Additionally, these vendors also help to mitigate the risk of costly cyber breaches and legal penalties by ensuring compliance.
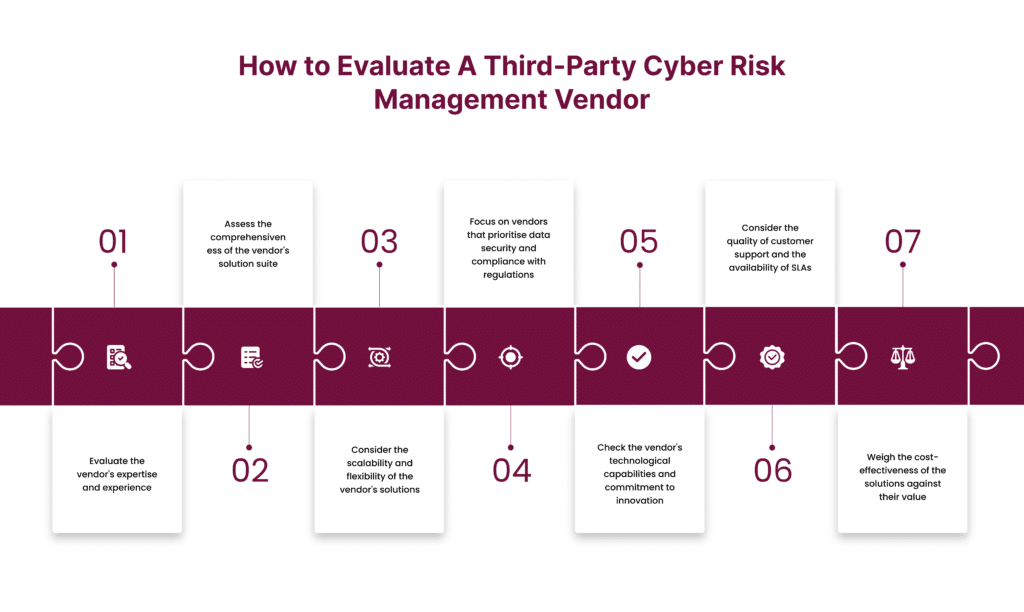
Choose Wisely: Steps To Evaluate And Select A Third-Party Cyber Risk Management Vendor
Choosing the right vendor for third-party cyber risk management is crucial in safeguarding your organisation’s integrity, confidentiality, and availability of sensitive data. This is a critical decision that requires careful evaluation. Here are some key factors to consider when making this choice:
Expertise and Experience
Evaluate the vendor’s expertise and experience in the field of third-party cyber risk management. Look for vendors with a proven track record of helping organisations across various industries effectively mitigate vendor-related risks. Consider factors such as the vendor’s industry certifications, client testimonials, and case studies showcasing successful implementations.
Comprehensive Solution Suite
Assess the comprehensiveness of the vendor’s solution suite. Look for vendors that offer a holistic approach to third-party risk management, encompassing risk assessment, vendor profiling, continuous monitoring, and incident response capabilities. Ensure that the vendor’s solutions align with your organisation’s specific requirements and compliance mandates.
Scalability and Flexibility
Consider the scalability and flexibility of the vendor’s offerings. As your organisation grows and your vendor ecosystem expands, you will need a solution that can accommodate evolving needs and scale accordingly. Evaluate whether the vendor’s solutions can adapt to changes in your business requirements and support integration with existing systems and processes.
Data Security and Compliance
Focus on vendors that prioritise data security and compliance with regulatory requirements like GDPR and DPDP. Ensure that the vendor adheres to industry best practices and standards for information security, such as ISO 27001 and SOC 2 compliance. Additionally, verify the vendor’s approach to data privacy and how they handle sensitive information shared during the engagement.
Technology and Innovation
Assess the vendor’s technological capabilities and commitment to innovation. Look for vendors that leverage advanced technologies such as artificial intelligence, machine learning, and automation to enhance their risk management processes. Evaluate the vendor’s roadmap for future enhancements and how they stay informed of emerging cyber threats and trends.
Customer Support and Service Level Agreements (SLAs)
Consider the quality of customer support and the availability of service level agreements (SLAs). Ensure that the vendor provides responsive support and assistance in implementing and configuring their solutions. Review the SLAs to understand the vendor’s commitments regarding uptime, issue resolution times, and escalation procedures.
Cost and ROI
Evaluate the cost-effectiveness of the vendor’s solutions with the value they deliver. Consider factors such as licensing fees, implementation costs, and ongoing maintenance expenses. Assess the potential return on investment (ROI) in terms of risk reduction, operational efficiencies, and mitigation of potential security incidents.
The role of third-party cyber risk management vendors cannot be overstated in today’s complex cybersecurity landscape. Investing in the right third-party risk management vendor is not just a sound business decision, it is a crucial step towards protecting your organisation’s assets, maintaining trust with stakeholders, and strengthening resilience in the face of evolving cyber threats. With the right partnerships in place, your organisation can navigate the intricacies of third-party relationships with confidence, knowing it has strong allies to defend against cyber adversaries.