ConnectSecure’s vulnerability management solution automates the tasks of managing vulnerabilities for you, so you can focus on catering to other needs of your clients.








As cyberattacks grow to threaten businesses of all sizes, it can become challenging for managed service providers to keep up and defend their clients’ systems from these attacks. Designed in collaboration with certified managed service providers, ConnectSecure offers automated vulnerability management solutions that allow you to stay one step ahead of evolving vulnerabilities, reducing cyber risks, and protecting your clients’ data.


Proactively identify and address security weaknesses, and ensure that software vulnerabilities are promptly addressed.

Ensure your clients comply with PCI DSS, HIPAA, GDPR IV, NIST 800-53, NIST 800-171, CIS, CIS 8.0, ISO 27002, Cyber Essentials, and Essential Eight.

Safeguard personal information from cyber threats, ensuring the privacy and security of individuals and organisations.




Proactively identify and address security weaknesses, and ensure that software vulnerabilities are promptly addressed.

Ensure your clients comply with PCI DSS, HIPAA, GDPR IV, NIST 800-53, NIST 800-171, CIS, CIS 8.0, ISO 27002, Cyber Essentials, and Essential Eight.

Safeguard personal information from cyber threats, ensuring the privacy and security of individuals and organisations.

Provide enhanced protection with in-built EPSS (Exploit Prediction Scoring System) against evolving cyber threats.


Perform external Deep Attack Surface Scans to identify and address vulnerabilities in digital infrastructure and enhance overall security.







Use on-site and Azure AD scanning to detect and prevent unauthorized access, enforce MFA, and provide Office 365 Risk Scoring.

Leverage the power of comprehensive software system assessment to mitigate vulnerabilities, and monitor required and denied software services across all assets.

Use a drag-and-drop model to create well-designed, customised reports in MS Office formats for technical and management reviews (including a white label option).
While maintaining the security of client systems, it often becomes tedious for MSPs to use multiple tools to get the job done. ConnectSecure’s purpose-built tool is an all-in-one B2B cybersecurity platform that is designed for your ease of use, so you can offer robust & prompt services for your clients.
While maintaining the security of client systems, it often becomes tedious for MSPs to use multiple tools to get the job done. ConnectSecure’s purpose-built tool is an all-in-one B2B cybersecurity platform that is designed for your ease of use, so you can offer robust & prompt services for your clients.
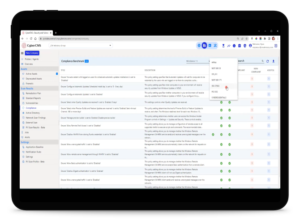


Maintain strong security by having a clear view of everything. Using ConnectSecure, you can perform vulnerability scans on hardware, software, networks, open ports, exposed systems, and much more. Whether it’s a one-time check or an ongoing automated process, expert-curated scans minimise false alerts, giving you accurate results.

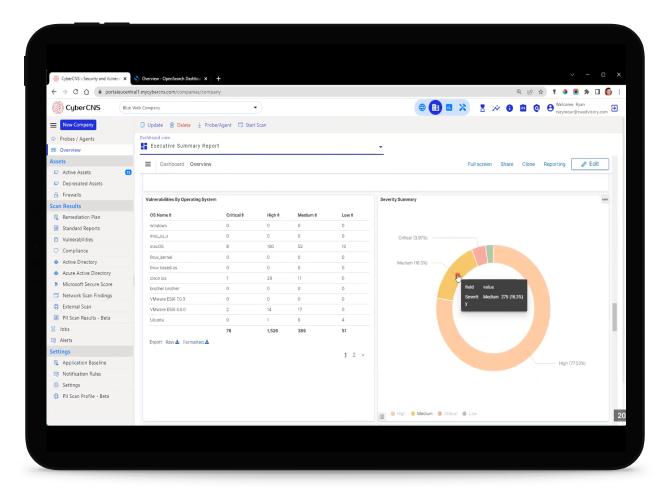
High-risk vulnerabilities require immediate action. ConnectSecure categorises everything, so you always know what should be prioritised. It is a single, multi-tenant interface for all your clients and assets gives you instant access to the information you need to activate vulnerability remediation with minimal effort.

Easy-to-understand reporting is essential for busy MSPs. ConnectSecure allows you to customise the look and feel of your dashboard to represent your business. With automated reporting, ConnectSecure does all the hard work for you, while you focus on maintaining relations with your clients.
ConnectSecure empowers you to position yourself as the partner every small to medium-sized business needs to thrive in an increasingly complex threat and compliance landscape.
ConnectSecure automates several tasks involved in vulnerability management, freeing up your team to focus on other critical tasks.
Upsell cybersecurity services, retain clients, and increase sales; ConnectSecure fosters scalability to accommodate your needs.
Build trust with your clients by showing you understand the significance of automated vulnerability management and compliance.







